Security Lapse at Dating App Raw Exposed User Data
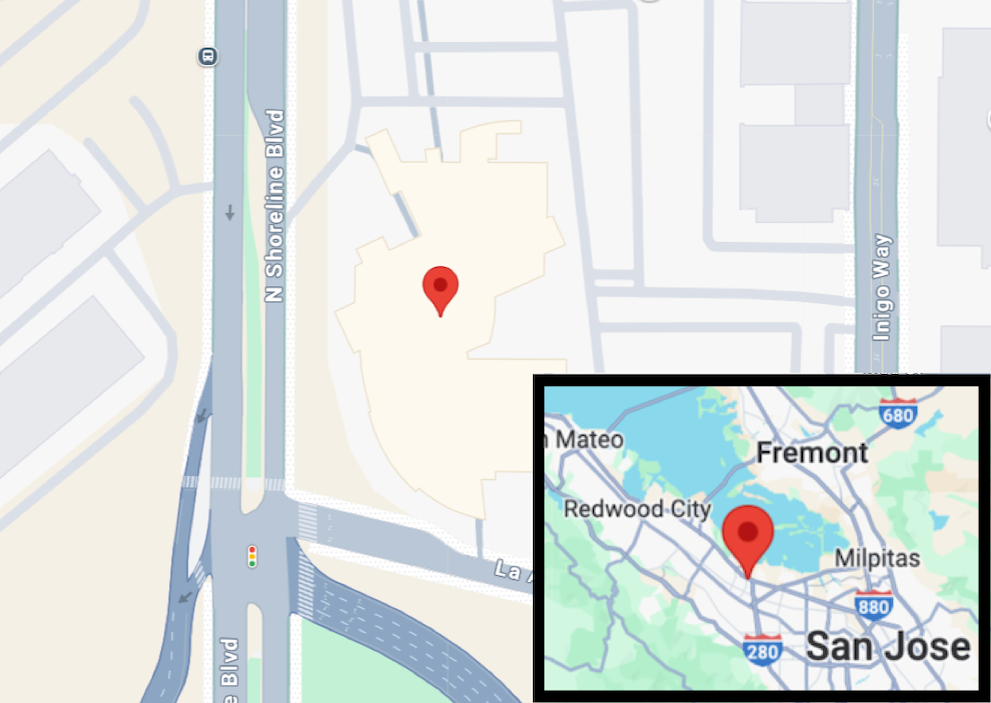
A security lapse at the dating app Raw publicly exposed the personal data and private location data of its users, as discovered by TechCrunch. The exposed data included users’ display names, dates of birth, dating and sexual preferences associated with the Raw app, as well as users’ locations. Some of the location data included coordinates specific enough to locate Raw app users with street-level accuracy.
Privacy Concerns with Raw App and Raw Ring
Raw, a dating app that launched in 2023, introduced a hardware extension called the Raw Ring. This unreleased wearable device is designed to track a partner’s heart rate and other sensor data to provide AI-generated insights, purportedly to detect infidelity. Despite moral and ethical concerns about tracking romantic partners, Raw assures users of end-to-end encryption for data security. However, TechCrunch’s investigation revealed that the app was publicly sharing user data without encryption, leading to a security breach that was promptly addressed by Raw.
Discovery of the Exposed Data
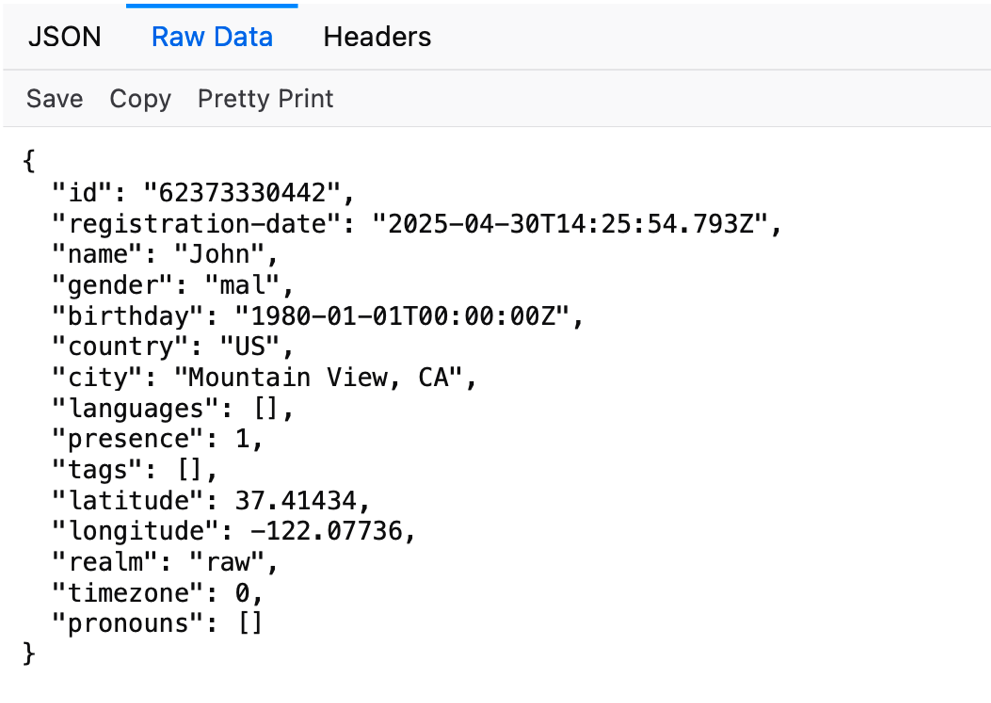
TechCrunch uncovered the data exposure during a test of the Raw app, where it was found that personal information could be accessed through an unprotected server link. By manipulating the unique identifier associated with each user’s profile, including location data, TechCrunch demonstrated the vulnerability of the app’s data security measures. Raw subsequently fixed the issue after being notified by TechCrunch, emphasizing the importance of rigorous security protocols in dating apps and wearable technology.
Understanding Insecure Direct Object References (IDOR)
This kind of vulnerability is known as an insecure direct object reference, or IDOR, a type of bug that can allow someone to access or modify data on someone else’s server because of a lack of proper security checks on the user accessing the data.
The Risks of IDOR Bugs
As we’ve explained before, IDOR bugs are akin to having a key to a private mailbox, for example, but that key can also unlock every other mailbox on that same street. As such, IDOR bugs can be exploited with ease and in some cases enumerated, allowing access to record after record of user data.
U.S. cybersecurity agency CISA has long warned of the risks that IDOR bugs present, including the ability to access typically sensitive data “at scale.” As part of its Secure by Design initiative, CISA said in a 2023 advisory that developers should ensure their apps perform proper authentication and authorization checks.
Addressing the Issue
Since Raw fixed the bug, the exposed server no longer returns user data in the browser.